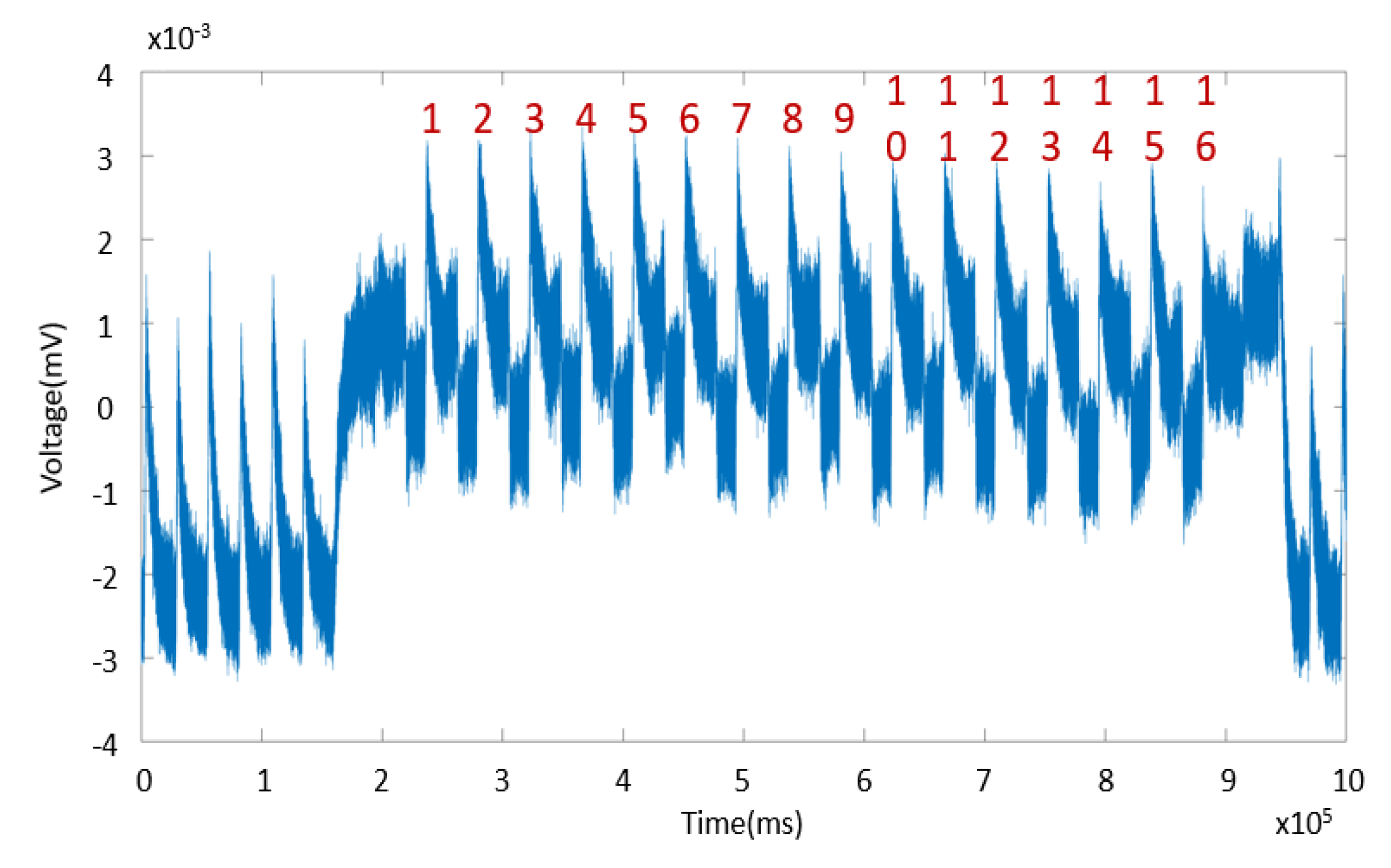
Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman
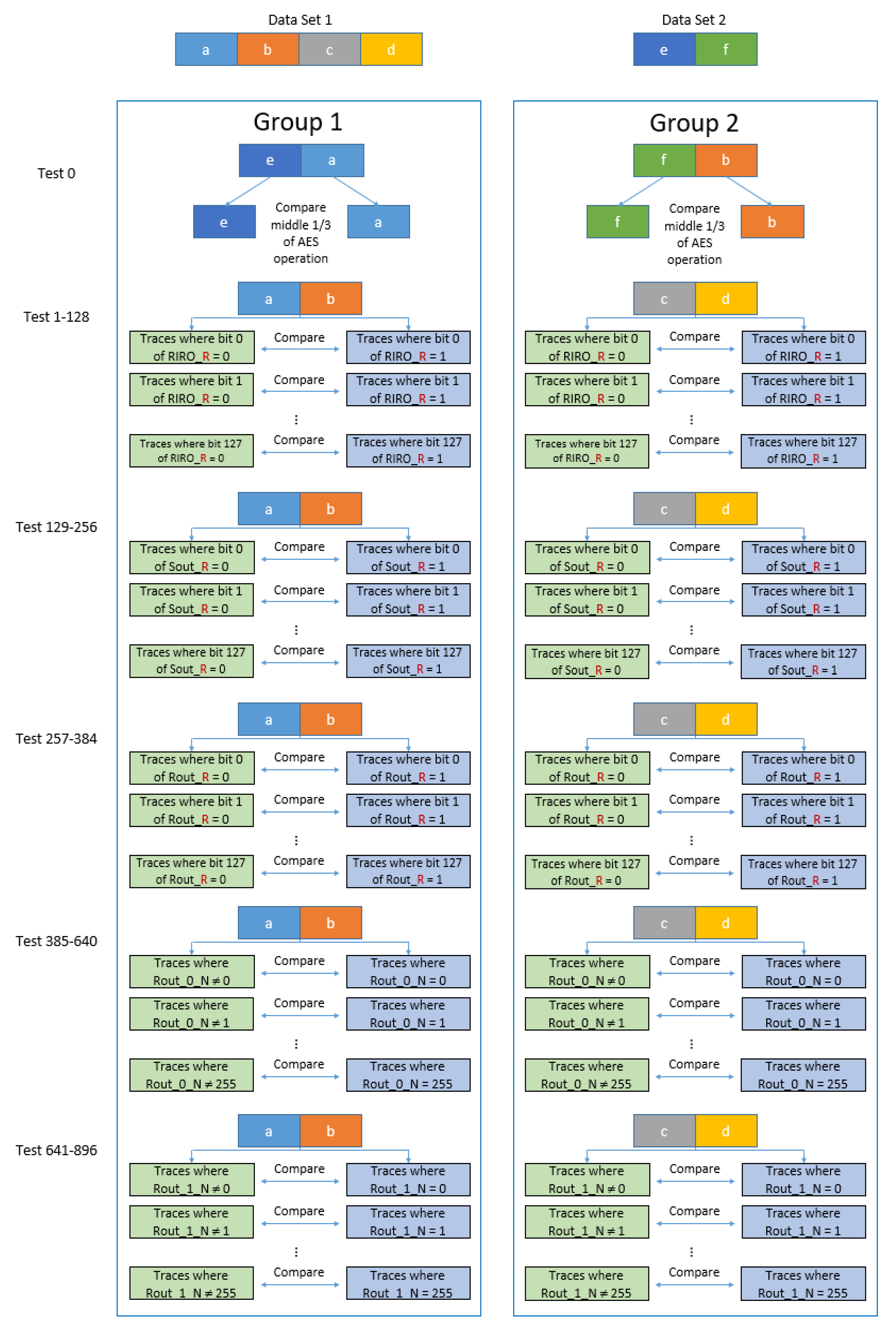
Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman
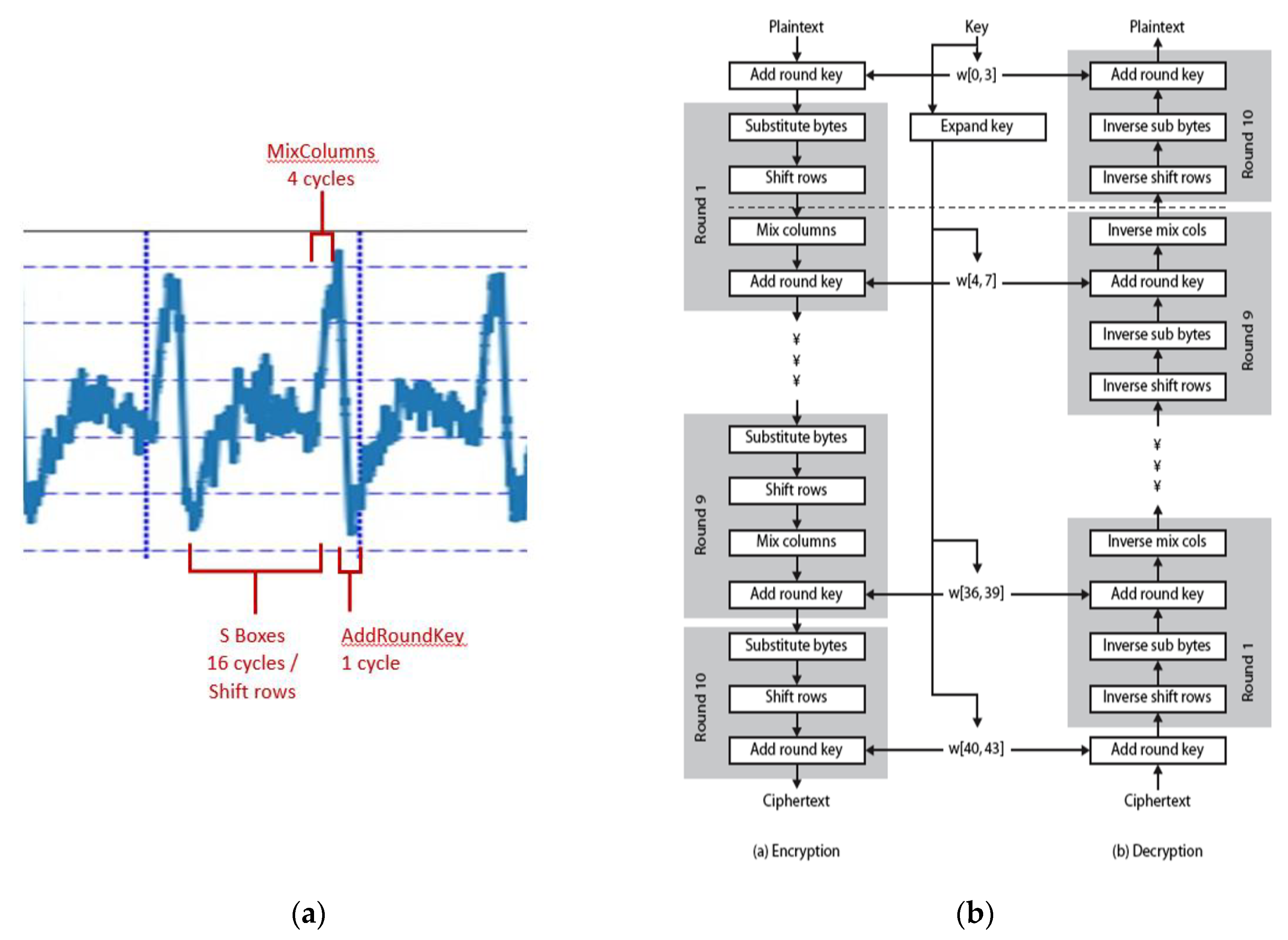
Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman











